Life online can differ wildly from the real world—especially when security is involved. It’s not likely someone will break into your home if you lose your house keys. But leaked login info? That puts a target on your back. Case in point: Last week, Roku disclosed a whopping 576,000 users were victims of a credential stuffing attack, far exceeding the original 15,000 accounts first reported in mid-March.
Credential stuffing involves plugging in usernames and passwords taken from data leaks and breaches into various websites. Hackers can do so quickly and efficiently through automation, as illustrated by the half-million accounts affected by this campaign. The attackers behind this Roku breach ultimately bought streaming service subscriptions and Roku hardware products through several hundred accounts with payment info on file.
In response, Roku has reversed those unauthorized charges—and also enabled its method of two-factor authentication on all accounts. Users must now click an emailed verification link to complete login.
These steps are all the right ones, except for one part—the fact that people reuse passwords, making this kind of hack possible and the subsequent remediations necessary. If more people had stored payment information in their Roku profiles, the damage could have been far more extensive, even if the 576,000 users caught up in this hack were just a fraction of Roku’s 80 million active accounts.
Fact of the matter is, reusing passwords in today’s environment is about as useful as a doorknob lock. They’ll keep out casual lurkers, but not anyone with determination to get in. Weak passwords are just as bad, since computers can crack or guess simple passwords with stunning ease.
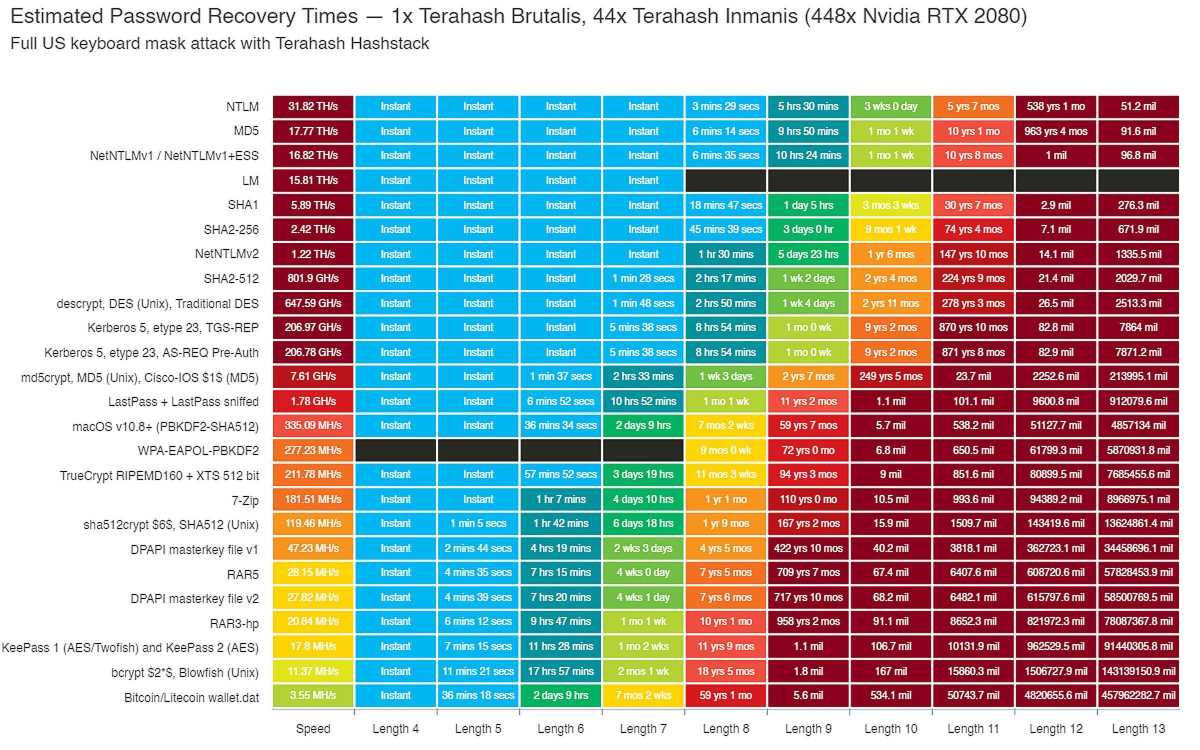
As this picture from 2021 illustrates, hundreds of graphics cards can be combined to crack passwords. The longer the password is, the stronger it is, even when accounting for the big leaps in speed of newer graphics cards.
Terahash / X
The most dangerous scenario is if a reused, weak, or easily guessed password works on one of your financial accounts—a hacker could make off with your life savings with little effort. At best, you’ll get your money back after appealing to your bank, but at worst, you could be left on the hook for the loss.
Not far behind are shopping sites, where it’s more common to keep stored payment information on file. Someone could quickly rack up hundreds (if not thousands) of fraudulent charges in your name, leaving you to unravel the mess.
But even on sites that “only” hold more of your personal information, like your birthdate, physical address, phone number, or age, there’s risk. Bad actors can use those details for building a fuller profile of you and successfully pulling off social engineering attacks on your more sensitive or essential accounts.
If you do reuse passwords, it’s an easily fixed problem—and Roku’s security team perfectly modeled what you should do. First, change your passwords so that you end up with unique and strong passwords (the longer the better) for each site. A password manager will handle that work for you so it feels painless. Whether you choose a paid service or a free one, it will autogenerate passwords (and even user names), then save them.
Next, add two-factor authentication to your accounts as much as possible. Ideally, you’ll want to use a separate app from your password manager for the most security, but even if you store it in a compatible password manager, you’ve at least got it in place. At minimum, enable two-factor on any account that has personal information (or information that could give away your identity), and/or payment details.
Between these two moves, you’ll up your online security considerably. Just be sure to follow one big piece of advice: Always keep your passwords for your password manager and your primary email address memorized. Life can become a major hassle if you don’t.